Advanced Web Hacking Tools
A internet utility is a application or software program that runs on a internet browser to function unique tasks. Any internet software has countless layers – internet server, the content material of the software that is hosted on the internet server and the backend interface layer that integrates with different applications. Web utility structure is scalable and has elements which have excessive availability.
Ethical Hacking is the manner of the appropriating the net utility from its genuine person with the aid of tinkering in a range of ways. The net utility hacker wishes to have deep know-how of the net software structure to effectively hack it. To be a master, the hacker wants to practice, examine and additionally tinker with the application.
Web utility hacking requires tenacity, focus, interest to detail, statement and interfacing. There are many sorts of internet utility hacking, and many protection mechanisms reachable to counter and to shield the software from being hacked.
Core protection mechanisms
There are 4 classes in which we can defend the net application:
User get entry to coping with to the software facts and functionality
User enter coping with
Suitable shielding and offensive measures to frustrate the hacker
Application configuration to get the alert in case of unauthorized access
User Access
A net utility affords exclusive roles for consumer get right of entry to relying on the enterprise requirement and use cases. A basic instance is a digital banking scenario, the place the consumer needs to get admission to the banking features to get the stability from his account or switch the money to anyone else. Another instance is a situation the place a Linux administrator wishes to supply privileges and rights to licensed users.
The net software makes use of the beneath safety mechanisms:
Authentication
Session management
Access control
Authentication is figuring out a person to whom the credentials belong. This can be performed the use of is a person identify and password. Additional authentication can be performed thru the user's cell variety or biometrics.
Session administration is the procedure of the person being signed in throughout, whilst the use of the internet application. Every time the person logs in to use the application, it is recorded as a session. Sessions can differ relying on the use case and application.
Access manipulate is a method of defending the HTTP requests in Web application. This is the closing layer of protection in the consumer access.
User Input
All the consumer inputs in the net utility are continually untrusted. A internet software need to have protection mechanisms in vicinity to stop the person from writing malicious code or breaking the website. We can cope with the person enter validation at a number degrees based totally on the want of the business.
Input managing to reject all phrases associated to hacking- this is a system of blacklisting them which the net server will test and confirm. These are known as Semantic Checks.
Also growing a set of policies to take delivery of the person inputs – for example, solely numbers that are secure for Bank account get right of entry to can be used. This is known as Safe Data Handling.
We want to have multi-step validation the place each and every issue is checked for person inputs in the net application.
We can have boundary validation to test all the exterior interfaces with the applications.
Handling Hackers
To get extra touchy signals in the net software we want to have following
Audit logs records
IP tackle blocking
Intrusion Detection systems
Firewalls
We want to have utility configuration with the key alert that has to be notified straight away when any hacker receives into the net application.
Web software technologies
The pinnacle net applied sciences that builders are the usage of for net improvement are as below:
HTML
CSS
Programming Languages
jаvascript
Coffee Script
Python
Ruby
PHP
GO
Objective C
SWIFT
Java
Frameworks
Node.JS
Ruby on Rails
Django
Ionic
Phonegap
Bootstrap
Foundation
Wordpress
Drupal .
NET
Angular JS
Ember JS
Backbone JS
Libraries
J Query
Underscore
Database
MongoDB
Redis
Postgres SQL
MySQL
Oracle
SQL Server
Data Formats
JSON
XML
CSV
Protocols
HTTP
DDP
REST
Digital Technologies for Web Applications
Web Assembly – comparable to jаvascript
Movement UI Design
Chabot's
Artificial Intelligence
Dynamic Web Applications – PWA
Blockchain
Single Page Applications
Web Server Software
Computerized Transformation
AMP Wins
VR and AR
Symfony
Laravel
Bypassing client-side controls
The procedure of sending records from server to consumer is very frequent in net applications. The reverse is additionally proper when customer sends the statistics to the server. It is regular for software program builders to expect that the customer will now not adjust the data. Avoiding the storage of records inside the person session can assist in protection and additionally expand performance. Modifying the records saved in the purchaser aspect is convenient in evaluation to the server aspect by means of the hacker.
Two methods exist for bypassing:
Application depends on client-side information to preclude the person input. So, limiting the patron facet controls the security.
Application gathers facts that is entered via user, the consumer implements techniques to manage the preceding data.
For each the options, the following are the strategies to by-pass consumer facet controls:
HTML structure features
Client Side Scripts
Thick Client technologies
Authentication and Authorization
Web functions have each authentication and authorization as key principles assisting the internet applications.
Authentication refers to any verification method that assessments whether or not a human or computerized device is who or what it claims to be. Authentication is the manner of verifying the identification of the individual. A special identifier is delivered for the internet utility like Password, Login or username. We can use OpenID, OAUTH, and SAML. The whole Authentication relies upon on the HTTP/HTTPS implementation.
Authorization is a procedure in which we have controls to enable or preclude resources. It is totally based on commercial enterprise use instances and it varies quit to end. For strengthening the authorization we have to put in force logging for all privileged actions. Invalid classes have to be made to log out.
So we want to have strict controls on each the standards to forestall hacking of net applications.
XSS – Cross website online scripting
This is a kind of injection in which malicious scripts are injected to depended on websites. A hacker makes use of a net utility to ship malicious code. This is in the structure of browser-side script. The stop consumer has no way to understand that a hacker has entered into the net utility and he continues to execute the script. Script can get right of entry to cookies, session tokens and all different touchy facts and even have the functionality to rewrite the whole HTML web page content.
Types of XSS
Stored XSS
Reflected XSS
DOM based totally XSS
All these can happen in Client XSS or Server XSS.
Bypassing blacklists and whitelists
Blacklist refers to the exercise of no longer permitting positive addresses and blocking off them primarily based on the want and requirement. They can be IP address, Networks and URLs.
Whitelist shows that a server would solely permit via requests that include a URL on an time-honored list, and different requests will fail.
Whitelist are more difficult to pass by as they are default controls in the internet application. The idea is that it redirects to the inside URL. We can pass by a blacklist by
Fooling it with redirects
Tricking with DNS
IPV6 tackle usage
Switching out the encoding
Hex Encoding
Octal Encoding
Dword Encoding
URL Encoding
Mixed Encoding
CSRF – Cross web page request forgery
CSRF is an assault that forces an cease consumer to execute undesirable moves on a net software which is already authenticated. The hacker can ship a hyperlink by means of an electronic mail and chat, and may additionally trick the customers of a net software into executing actions. In case the assault is on an administrator account the complete net utility can be compromised.
Unvalidated redirects
These are viable when a net utility accepts untrusted input. This can purpose the internet software to redirect the request to a URL containing untrusted inputs. Through the change of the Untrusted URL enter to a malicious site, the hacker launches a phishing assault and steals the person credentials.
These redirects the use of credentials can additionally provide the hacker the privilege features which commonly they can't access.
We want to have the person grant a quick name, ID or token which is mapped server-side to a full goal URL and this offers safety to the whole process.
SQL injection
SQL injection is a procedure of injecting the malicious SQL question by the enter records from the customer to the net application.
SQL injection can modify, read, and delete the touchy facts from the Databases.
Has the capability to problem instructions to the working system
Administration controls on the operations of the database
Done thru easy SQL commands
File add vulnerabilities
Web functions have these functionalities and elements of importing files.
These documents can be text, pictures, audio, video and different formats.
We want to be cautious whilst importing files.
A hacker can ship a faraway shape Data POST request with mime kind and execute the code.
With this, the archives add will be managed via the hacker.
Attacking the software server
The more than a few codecs of the assaults on the utility server are listed below:
Cross-Site Scripting (XSS)
SQL Injection (SQLi)
File add
Local File Inclusion (LFI)
Distributed Denial of Service (DDoS)
Web software hacker's toolkit
The hacker's toolkit is as given below:
Intercepting Web proxy – Modifies all HTTP messaging between browser and internet application
Web utility scanner - For the hacker to get the whole records about the internet application.
A few of the equipment which belong to the above two categories:
Kali Linux
Angry IP Scanner
Cain & Abel
Ettercap
Burp Suite
John the Ripper
Metaspoilt
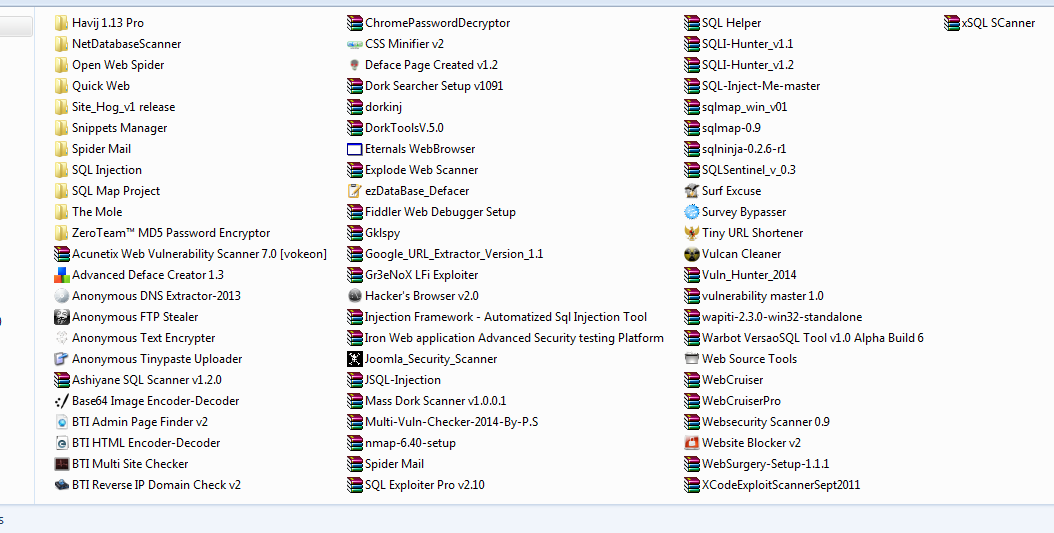
Download now:)
Tools Contains:
Havij
NetDatabaseScanner
Open Web Spider
Quick Web
Site Hog
Snippets Manager
Spider Mail
SQL Injection
SQL Map Project
The Mole
ZeroTeam™ MD5 Password Encryptor
Acunetix Web Vulnerability Scanner
Advanced Deface Creator 1.3
Anonymous DNS Extractor-2013
Anonymous FTP Stealer
Anonymous Text Encrypter
Anonymous Tinypaste Uploader
Ashiyane SQL Scanner
Base64 Image Encoder-Decoder
BTI Admin Page Finder v2
BTI HTML Encoder-Decoder
BTI Multi Site Checker
BTI Reverse IP Domain Check v2
ChromePasswordDecryptor
CSS Minifier v2
Deface Page Created
Dork Searcher Setup v1091
dorkinj
DorkTools
Eternals WebBrowser
Explode Web Scanner
ezDataBase_Defacer
Fiddler Web Debugger Setup
Gklspy
Google URL Extractor
Gr3eNoX LFi Exploiter
Hacker's Browser v2.0
Injection Framework – Automatized Sql Injection Tool
Iron Web application Advanced Security testing Platform
Joomla Security Scanner
JSQL-Injection
Mass Dork Scanner v1.0.0.1
Multi Vuln Checker
nmap
Spider Mail
SQL Exploiter Pro v2.10
SQL Helper
SQLI-Hunter_v1.1
SQLI-Hunter_v1.2
SQL-Inject-Me-master
sqlmap_win_v01
sqlmap-0.9
sqlninja-0.2.6-r1
SQLSentinel_v_0.3
Surf Excuse
Survey Bypasser
Tiny URL Shortener
Vulcan Cleaner
Vuln Hunter
vulnerability master
wapiti-2.3.0-win32-standalone
Warbot VersaoSQL Tool v1.0 Alpha Build 6
Web Source Tools
WebCruiser
WebCruiserPro
Websecurity Scanner 0.9
Website Blocker v2
WebSurgery-Setup-1.1.1
XCodeExploitScannerSept
xSQL SCanner
Advanced Web Hacking Tools

A internet utility is a application or software program that runs on a internet browser to function unique tasks. Any internet software has countless layers – internet server, the content material of the software that is hosted on the internet server and the backend interface layer that integrates with different applications. Web utility structure is scalable and has elements which have excessive availability.
Ethical Hacking is the manner of the appropriating the net utility from its genuine person with the aid of tinkering in a range of ways. The net utility hacker wishes to have deep know-how of the net software structure to effectively hack it. To be a master, the hacker wants to practice, examine and additionally tinker with the application.
Web utility hacking requires tenacity, focus, interest to detail, statement and interfacing. There are many sorts of internet utility hacking, and many protection mechanisms reachable to counter and to shield the software from being hacked.
Core protection mechanisms
There are 4 classes in which we can defend the net application:
User get entry to coping with to the software facts and functionality
User enter coping with
Suitable shielding and offensive measures to frustrate the hacker
Application configuration to get the alert in case of unauthorized access
User Access
A net utility affords exclusive roles for consumer get right of entry to relying on the enterprise requirement and use cases. A basic instance is a digital banking scenario, the place the consumer needs to get admission to the banking features to get the stability from his account or switch the money to anyone else. Another instance is a situation the place a Linux administrator wishes to supply privileges and rights to licensed users.
The net software makes use of the beneath safety mechanisms:
Authentication
Session management
Access control
Authentication is figuring out a person to whom the credentials belong. This can be performed the use of is a person identify and password. Additional authentication can be performed thru the user's cell variety or biometrics.
Session administration is the procedure of the person being signed in throughout, whilst the use of the internet application. Every time the person logs in to use the application, it is recorded as a session. Sessions can differ relying on the use case and application.
Access manipulate is a method of defending the HTTP requests in Web application. This is the closing layer of protection in the consumer access.
User Input
All the consumer inputs in the net utility are continually untrusted. A internet software need to have protection mechanisms in vicinity to stop the person from writing malicious code or breaking the website. We can cope with the person enter validation at a number degrees based totally on the want of the business.
Input managing to reject all phrases associated to hacking- this is a system of blacklisting them which the net server will test and confirm. These are known as Semantic Checks.
Also growing a set of policies to take delivery of the person inputs – for example, solely numbers that are secure for Bank account get right of entry to can be used. This is known as Safe Data Handling.
We want to have multi-step validation the place each and every issue is checked for person inputs in the net application.
We can have boundary validation to test all the exterior interfaces with the applications.
Handling Hackers
To get extra touchy signals in the net software we want to have following
Audit logs records
IP tackle blocking
Intrusion Detection systems
Firewalls
We want to have utility configuration with the key alert that has to be notified straight away when any hacker receives into the net application.
Web software technologies
The pinnacle net applied sciences that builders are the usage of for net improvement are as below:
HTML
CSS
Programming Languages
jаvascript
Coffee Script
Python
Ruby
PHP
GO
Objective C
SWIFT
Java
Frameworks
Node.JS
Ruby on Rails
Django
Ionic
Phonegap
Bootstrap
Foundation
Wordpress
Drupal .
NET
Angular JS
Ember JS
Backbone JS
Libraries
J Query
Underscore
Database
MongoDB
Redis
Postgres SQL
MySQL
Oracle
SQL Server
Data Formats
JSON
XML
CSV
Protocols
HTTP
DDP
REST
Digital Technologies for Web Applications
Web Assembly – comparable to jаvascript
Movement UI Design
Chabot's
Artificial Intelligence
Dynamic Web Applications – PWA
Blockchain
Single Page Applications
Web Server Software
Computerized Transformation
AMP Wins
VR and AR
Symfony
Laravel
Bypassing client-side controls
The procedure of sending records from server to consumer is very frequent in net applications. The reverse is additionally proper when customer sends the statistics to the server. It is regular for software program builders to expect that the customer will now not adjust the data. Avoiding the storage of records inside the person session can assist in protection and additionally expand performance. Modifying the records saved in the purchaser aspect is convenient in evaluation to the server aspect by means of the hacker.
Two methods exist for bypassing:
Application depends on client-side information to preclude the person input. So, limiting the patron facet controls the security.
Application gathers facts that is entered via user, the consumer implements techniques to manage the preceding data.
For each the options, the following are the strategies to by-pass consumer facet controls:
HTML structure features
Client Side Scripts
Thick Client technologies
Authentication and Authorization
Web functions have each authentication and authorization as key principles assisting the internet applications.
Authentication refers to any verification method that assessments whether or not a human or computerized device is who or what it claims to be. Authentication is the manner of verifying the identification of the individual. A special identifier is delivered for the internet utility like Password, Login or username. We can use OpenID, OAUTH, and SAML. The whole Authentication relies upon on the HTTP/HTTPS implementation.
Authorization is a procedure in which we have controls to enable or preclude resources. It is totally based on commercial enterprise use instances and it varies quit to end. For strengthening the authorization we have to put in force logging for all privileged actions. Invalid classes have to be made to log out.
So we want to have strict controls on each the standards to forestall hacking of net applications.
XSS – Cross website online scripting
This is a kind of injection in which malicious scripts are injected to depended on websites. A hacker makes use of a net utility to ship malicious code. This is in the structure of browser-side script. The stop consumer has no way to understand that a hacker has entered into the net utility and he continues to execute the script. Script can get right of entry to cookies, session tokens and all different touchy facts and even have the functionality to rewrite the whole HTML web page content.
Types of XSS
Stored XSS
Reflected XSS
DOM based totally XSS
All these can happen in Client XSS or Server XSS.
Bypassing blacklists and whitelists
Blacklist refers to the exercise of no longer permitting positive addresses and blocking off them primarily based on the want and requirement. They can be IP address, Networks and URLs.
Whitelist shows that a server would solely permit via requests that include a URL on an time-honored list, and different requests will fail.
Whitelist are more difficult to pass by as they are default controls in the internet application. The idea is that it redirects to the inside URL. We can pass by a blacklist by
Fooling it with redirects
Tricking with DNS
IPV6 tackle usage
Switching out the encoding
Hex Encoding
Octal Encoding
Dword Encoding
URL Encoding
Mixed Encoding
CSRF – Cross web page request forgery
CSRF is an assault that forces an cease consumer to execute undesirable moves on a net software which is already authenticated. The hacker can ship a hyperlink by means of an electronic mail and chat, and may additionally trick the customers of a net software into executing actions. In case the assault is on an administrator account the complete net utility can be compromised.
Unvalidated redirects
These are viable when a net utility accepts untrusted input. This can purpose the internet software to redirect the request to a URL containing untrusted inputs. Through the change of the Untrusted URL enter to a malicious site, the hacker launches a phishing assault and steals the person credentials.
These redirects the use of credentials can additionally provide the hacker the privilege features which commonly they can't access.
We want to have the person grant a quick name, ID or token which is mapped server-side to a full goal URL and this offers safety to the whole process.
SQL injection
SQL injection is a procedure of injecting the malicious SQL question by the enter records from the customer to the net application.
SQL injection can modify, read, and delete the touchy facts from the Databases.
Has the capability to problem instructions to the working system
Administration controls on the operations of the database
Done thru easy SQL commands
File add vulnerabilities
Web functions have these functionalities and elements of importing files.
These documents can be text, pictures, audio, video and different formats.
We want to be cautious whilst importing files.
A hacker can ship a faraway shape Data POST request with mime kind and execute the code.
With this, the archives add will be managed via the hacker.
Attacking the software server
The more than a few codecs of the assaults on the utility server are listed below:
Cross-Site Scripting (XSS)
SQL Injection (SQLi)
File add
Local File Inclusion (LFI)
Distributed Denial of Service (DDoS)
Web software hacker's toolkit
The hacker's toolkit is as given below:
Intercepting Web proxy – Modifies all HTTP messaging between browser and internet application
Web utility scanner - For the hacker to get the whole records about the internet application.
A few of the equipment which belong to the above two categories:
Kali Linux
Angry IP Scanner
Cain & Abel
Ettercap
Burp Suite
John the Ripper
Metaspoilt
Download now:)
Tools Contains:
Havij
NetDatabaseScanner
Open Web Spider
Quick Web
Site Hog
Snippets Manager
Spider Mail
SQL Injection
SQL Map Project
The Mole
ZeroTeam™ MD5 Password Encryptor
Acunetix Web Vulnerability Scanner
Advanced Deface Creator 1.3
Anonymous DNS Extractor-2013
Anonymous FTP Stealer
Anonymous Text Encrypter
Anonymous Tinypaste Uploader
Ashiyane SQL Scanner
Base64 Image Encoder-Decoder
BTI Admin Page Finder v2
BTI HTML Encoder-Decoder
BTI Multi Site Checker
BTI Reverse IP Domain Check v2
ChromePasswordDecryptor
CSS Minifier v2
Deface Page Created
Dork Searcher Setup v1091
dorkinj
DorkTools
Eternals WebBrowser
Explode Web Scanner
ezDataBase_Defacer
Fiddler Web Debugger Setup
Gklspy
Google URL Extractor
Gr3eNoX LFi Exploiter
Hacker's Browser v2.0
Injection Framework – Automatized Sql Injection Tool
Iron Web application Advanced Security testing Platform
Joomla Security Scanner
JSQL-Injection
Mass Dork Scanner v1.0.0.1
Multi Vuln Checker
nmap
Spider Mail
SQL Exploiter Pro v2.10
SQL Helper
SQLI-Hunter_v1.1
SQLI-Hunter_v1.2
SQL-Inject-Me-master
sqlmap_win_v01
sqlmap-0.9
sqlninja-0.2.6-r1
SQLSentinel_v_0.3
Surf Excuse
Survey Bypasser
Tiny URL Shortener
Vulcan Cleaner
Vuln Hunter
vulnerability master
wapiti-2.3.0-win32-standalone
Warbot VersaoSQL Tool v1.0 Alpha Build 6
Web Source Tools
WebCruiser
WebCruiserPro
Websecurity Scanner 0.9
Website Blocker v2
WebSurgery-Setup-1.1.1
XCodeExploitScannerSept
xSQL SCanner

.webp)
.png)


0 التعليقات:
إرسال تعليق