Download SpyMax v2.0 RAT 2022 Hack Mobiles Phone:)
It is the latest and best android rat tool to hack android devices over the internet. It is used by hackers to hack millions of android devices remotely.This android rat has the capability to hack and control thousands of android devices at a single time.It works smoothly from android version 1 to android version 9. It is a persistent android rat. You can hack your victim's mobile for the long term with this remote access tool.
What is SpyMax v2?
It is one of the favorite android device hacking tools for hackers. It is the android rat that can use to spy on others. You can spy on your kids, you can spy on your gf and you can spy on anyone by using this tool.
It is the latest version of SpyMax 1 RAT. There are many new features you will see that were not seen before in their previous version. It is also known as android spyware.
You can hack thousands of android mobiles and android tablets by using this best android rat. It is a publically free rat. I give you their download link at the end of this article.
It has many new features like the binding feature. By using its binding feature you will able to bind spymax 2.0 payload with any other app. Like you can bind its payload with any gaming app, with any social app, and with any kind of video app, etc.
You can collect all information about your victim from this android rat. You can live to see what your victim is doing, what your victim is speaking etc everything all to all.
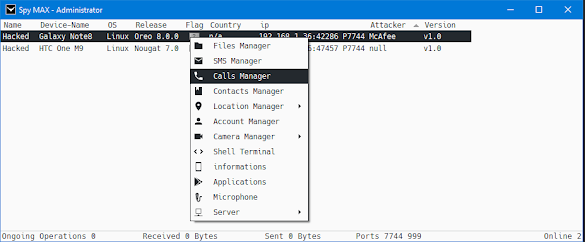
You can fully control victim mobile remotely by using spymax v2.0 cracked rat. You can grab your victims all SMS in 1 click from this best android rat.
You can grab your victim's mobiles all contacts list in 1 click. You can access your victim file manager remotely from this remote administration tool.
You can download and upload any file on your victim's mobile remotely by using this rat. You can execute any file on your victim's pc.
You can check the live location of your victim in real-time. You can also check how many apps installs on your victim pc.
You can install any app remotely in your victim's pc by using spymax 2.0 rat. You can get info about victims' mobile, their mobile model number, their mobile name, their mobile IMEI number, their mobile mac address, their cell phone number and etc many more.
Spymax v2.0 Cracked comes with easy to use GUI interface. It has many more powerful features than other remote administrations tools. It is based on android devices version 4 to android devices version 9 oreo.
It does not work smoothly on upper versions of android devices. It is an upgraded version of spymax series. You can download spymax for pc from below. It works on windows, not on android devices.
Many people waiting for spymax v3 upcoimg android rat but here I clear everyone doubts tha spymax v3 rat is not coming. Spymax series will skip spymax 3 versions and they will launch spymax v4 in future.
It works in stealth mode. Your victim will not know that he has been hacked by its stealth mode feature.It is malicious software classified as spyware. Its main target is all the devices using Android OS. It carries different features with which users like cybercriminals can monitor the infected device. It infects devices in the disguise, it’s very clever.
Today SpyMax Android RAT free download is being distributed via fake pharmacy sites and hospital sites in the form of an app known as COVIDTZ; this is not the only one that is disguising Spymax according to Jay Ferron from ChannelProNetwork.
It collects information from all the infected devices and installed ones. It is also able to monitor some of the system’s settings and covers other applications too. The latter one gives it with the priority over other running apps as it can overlay them or change their appearance.
- It can collect data relating to your browsing activity.
- Able to detect exact locations of the device, thus monitoring the user’s movements.
- It can check and modify the contact list.
- Monitor calls have control over the control features extensively; they can read as well as manage call logs and make direct calls on various numbers.
- It uses the device’s microphone to monitor or record conversations outside of calls.
- Misuses the camera of the device to click pictures and record videos.
- It can read SMS and MMS text SMS.
- Able to locate account linked with the device and misuse them potentially.
To put the long story short; this can lead to some severe issues. If such malware has infected your system, then it is recommended to remove it.
Inspite of spyware android OS devices can also be targeted by banking malware. Anubis, Eventbot and Cerberus are a few examples of this. Such infections can affect system health and lead to some serious security issues like theft and financial matters.
It is malicious software classified as spyware. Its main target is all the devices using Android OS. It carries different features with which users like cybercriminals can monitor the infected device. It infects devices in the disguise, it’s very clever.
Today SpyMax Android RAT free download is being distributed via fake pharmacy sites and hospital sites in the form of an app known as COVIDTZ; this is not the only one that is disguising Spymax according to Jay Ferron from ChannelProNetwork.
It collects information from all the infected devices and installed ones. It is also able to monitor some of the system’s settings and covers other applications too. The latter one gives it with the priority over other running apps as it can overlay them or change their appearance.
- It can collect data relating to your browsing activity.
- Able to detect exact locations of the device, thus monitoring the user’s movements.
- It can check and modify the contact list.
- Monitor calls have control over the control features extensively; they can read as well as manage call logs and make direct calls on various numbers.
- It uses the device’s microphone to monitor or record conversations outside of calls.
- Misuses the camera of the device to click pictures and record videos.
- It can read SMS and MMS text SMS.
- Able to locate account linked with the device and misuse them potentially.
To put the long story short; this can lead to some severe issues. If such malware has infected your system, then it is recommended to remove it.
Inspite of spyware android OS devices can also be targeted by banking malware. Anubis, Eventbot and Cerberus are a few examples of this. Such infections can affect system health and lead to some serious security issues like theft and financial matters.
Download :) Click hereClick the Button Below to Download the File.
Click the Button Below to Download the File.
Password :) majidzhacker.com
How To Use?
Many new coming peoples do not know how to use spymax v2.0 rat? I explain you in a simple way. Spy max download for pc link below.
You need port forwarding for this rat because It is working on TCP protocol. 2nd thing you need Is a dynamic hostname like ( noip and duck dns etc. )
Then use this information in spymax 2 cracked rat during the build and a payload successfully build and will work perfectly. I also provide you a practical video tutorial of SpyMax v2 RAT below.
New Improvements:)
- Able to fix sudden crash problems.
- The remote microphone has been fixed.
- Comes with a program connection speed that has been improved.
- Carries interfaces that are attractive and improved.
- The accuracy of GPS positioning is improved.
- Able to fix sudden crash problems.
- The remote microphone has been fixed.
- Comes with a program connection speed that has been improved.
- Carries interfaces that are attractive and improved.
- The accuracy of GPS positioning is improved.
How to Stay Safe from SpyMax Infection:)
For this you need to keep the following things in your mind:
- It would help if you exercised caution when you browse.
- Download content from channels that are official and verified.
- Activate and update products with tools or functions that are provided by genuine developers.
- Do not use illegal activation tools and third-party updaters; these can distribute malware.
- Do not open suspicious and irrelevant emails, especially the ones that have any attachments or links. All these may result in high-risk infections.
- Carry some well-reputed anti-virus or anti-spyware software installed in your android device.
- Keep device up to date.
- Run regular scans.
- Remove all detected threats and issues.
For this you need to keep the following things in your mind:
- It would help if you exercised caution when you browse.
- Download content from channels that are official and verified.
- Activate and update products with tools or functions that are provided by genuine developers.
- Do not use illegal activation tools and third-party updaters; these can distribute malware.
- Do not open suspicious and irrelevant emails, especially the ones that have any attachments or links. All these may result in high-risk infections.
- Carry some well-reputed anti-virus or anti-spyware software installed in your android device.
- Keep device up to date.
- Run regular scans.
- Remove all detected threats and issues.
(:Features:)
- Sms manager
- Screen capture
- Contacts manager
- Location manager
- GPS
- GSM
- Account manager
- Camera manager
- Front camera
- Back camera
- Shell terminal
- Phone Information
- Applications
- Fun
- Chat
- Microphone
- Call phone
- Clipboard
- Keylogger
- Server
- Ports
- Persistence
- Anti-sleep
- Icon
- Merge
- Doze
- Hide payload
- Bind payload
- Payload Melt
- Victim flag
- Settings
- Network
- Screenshot
- Fully license activated
- File manager
- Call manager
- Many more etc...
- Sms manager
- Screen capture
- Contacts manager
- Location manager
- GPS
- GSM
- Account manager
- Camera manager
- Front camera
- Back camera
- Shell terminal
- Phone Information
- Applications
- Fun
- Chat
- Microphone
- Call phone
- Clipboard
- Keylogger
- Server
- Ports
- Persistence
- Anti-sleep
- Icon
- Merge
- Doze
- Hide payload
- Bind payload
- Payload Melt
- Victim flag
- Settings
- Network
- Screenshot
- Fully license activated
- File manager
- Call manager
- Many more etc...
Revenge RAT Download v0.3 Latest Version 2022 :)
It is the best and powerful remote access trojan software to hack pc and laptops worldwide. It is used by blackhat hackers to hack thousands of users over the internet.t has the ability to handle up to thousands of victims' pc without any kind of lagging issue. It is the latest and best pc rat with many amazing features.How To Use?
Many newbies don't know how to use revenge rat software? It is very easy to use this remote access trojan software.You need port forwarding, your firewall and antivirus must be turned off, dynamic DNS properly set up on your windows. You can watch the complete practical video tutorial below.What is Revenge Malware?
Revenge belongs to the class of Remote Access Trojans which means that it is usually used by the attackers to control infected PCs remotely or spy on the users by monitoring keystrokes and even computer surroundings through the remote webcam and microphone access.
Discovered for the first time in 2016, Revenge RAT continues to be a threat at the present day with a big spike in popularity monitored in 2019, when the malware was observed targeting corporations and government structures all around the world in a massive malicious campaign codenamed “Aggah”. Thanks to a large variety of distribution methods similar to ransomware, robust core feature-set, and solid persistence mechanisms, Revenge has become a popular choice for cybercriminals. The popularity of this RAT was further aided by its open-source nature – anybody can freely download Revenge on underground hacking forums and employ it in their own campaigns.
It has come with so many powerful plugins that make your work very easy. You will see any kind of plugins like microphone plugin, password recovery plugins, remote webcam plugin, remote desktop plugin, and many more, etc.It also allows you to code your own custom plugin in this rat trojan software. It doesn't require physical access to your victim's device.Simply make a cracked revenge rat malware and send that malware to your targeted victim anywhere in the world.When your victim will install your rat malware in his pc then his pc will get hacked fully and silently and you can do anything from his pc with the help of this remote access trojan.You can view the live webcam of your targeted victim. You can hear the voice of your targeted victim in real-time through his pc mic.It allows you to control your desktop remotely through your mouse and keywords. You can steal all passwords from your victim pc silently that including their social media accounts login details, bank sites login details, and other websites login details.You will also see a binder feature in this remote access tool that helps you to bind your rat trojan payload with any file like software, image, video, etc.Binding will decrease the detection rate of your victim. Your targeted victim will not doubt on you that you bound any rat trojan payload with this file because when he runs that bound payload file then the payload executes silently in the background and the original file will show on that desktop screen.You can execute any file silently on your victim's pc with this remote administration tool. You can change the desktop wallpaper of your victim's pc.How to setup revenge rat software? It is very easy to set up the same as other remote access trojans software. Open its builder and enter your port number, DNS, and check other fields according to your choice and then click on build.It allows you to add multiple DNS in payload during building that helps you in that case, for example, if your one DNS is not working or suspended then you can use another one to get the connection back with your victim's device.I recommended you use DuckDns and Noip together for better results. These two are the best free DNS provides for rat hacking.RevengeRAT allows you to grab the logs from your victim's pc. You can also view the live location on the map of your victim's through its client map feature button.You will also see a USB spreader feature in this windows rat software that makes it better than other pc rats. It allows you to spreader your victim from pc to pc through pen drives.For example, you install your RevengeRAT payload on your friend's pc. When some insert his Pendrive in your friend's pc then your payload virus will automatically transfer his copy into his Pendrive.When he will insert back his Pendrive into his pc then your payload will also install on his pc, your virus will spread from pc to pc with the help of Pendrive through the revenge rat v0.3 usb spreader feature.Download :) Click here
Click the Button Below to Download the File.
General description of Revenge:)
The Revenge RAT was first observed in the wild in June 2016, when it was released by a user with a nick Napoleon – an Arabic-speaking member of the underground hacking community.
The initial version of this malware was a simple malicious program that didn’t offer much, if any, code obfuscation and was mainly used by other Arabic-speaking cybercriminals. Despite the simplicity of the malware, at the time, only one out of 54 of VirusTotal scanners could pick up the malicious nature of the Revenge code, which confused the researchers bearing in mind the lack of anti-analysis techniques.
The creator used Visual Basic to develop this RAT and personally admitted that the malware was very bare-bones at the time of its initial release– providing only the most basic functions and definitely losing to competitors in terms of core feature-set. According to Napoleon, this explained why Revenge was available free of charge.
After two months since the initial release, a new version v0.2 was issued by the author, on a more popular hacking forum, this time with more features, but still offered completely free of charge. Since then Revenge has evolved even further and today, it offers cybercriminals a wide range of capabilities including remote files and registry alterations on an infected machine, access to memory, processes, and services as well as access to connected devices such as keyboards, webcams, and mice, allowing this malware to record the actions of its victims and collect information like banking credentials and social account data.
Core malicious feature-set was not the only thing that evolved over the course of the Revenge lifetime. Improvements in distribution and persistence made this threat truly a force to be reckoned with. In some campaigns, scripts were executed in the HTML of a custom Blogspot [com] page.
Revenge RAT Features:)
- GUI
- Easy to use
- Plugins
- Bugs fixed
- Improvements
- Thumbnails
- Clients map
- Clients logs
- Client builder
- Support multiple DNS
- Execute any script and file
- Open any URL
- Reverse proxy
- Make your own plugins
- Easily customizable
- Professional looking
- Stop and terminate background tasks
- Uninstall any program from victim's pc
- Change registry settings
- Persistence
- Auto-startup
- Build virus in any executable form
- Built-in icons
- Options
- Blacklist
- CPU
- RAM
- Country name
- Operating system
- WAN / LAN
- File manager
- Remote cam
- Remote webcam
- Microphone
- Download
- Upload
- Password stealer
- Change desktop wallpaper
- Many more.
How To Install AndroRAT In Windows?
1. First of all Turn Off your antivirus2. Download and extract the zip file3. Now unzip it4. Turn off windows defender real-time protection5. Run Revenge RAT v0.3.Exe6. Enjoy.