Dork Generator: Simplifying Website Vulnerability Assessment:
1. Introduction
2. What is a Dork generator?
3. How does the Dork generator work?
4. Importance of Dork generators in website vulnerability assessment
5. Effective use of Dork generators
6. Features of Dork generators
7. 4 Advantages of using Dork generators Limitations and risks of Dork generators
9. Best practices for using Dork generators
10. The future of Dork generators
Login:
In the cybersecurity industry, web vulnerability assessment plays an important role in identifying potential weaknesses and ensuring overall online security. The Dork Generator is a powerful tool that helps with this process. This article will examine what Dork Generator is, how it works, its importance in vulnerability assessment, best practices for its use, and its future prospects.
What is a Dork generator?
A dork generator is a software tool or script designed to create advanced search queries (called "dorks") that can be used to discover malicious websites or specific information. These idiots use search engines to refine searches and identify websites that may have vulnerabilities.
How does a Dork generator work?
The Dork generator works by automating the process of creating complex questions. Using search operators such as “inurl,” “in title,” and “filetype,” they can narrow down search results and find sites that match specific criteria. This process may involve sensitive web applications, disclosures, or other sensitive information that should not be made publicly available.
Dork Generators play an important role in assessing the vulnerability of a website. It allows cybersecurity professionals to effectively investigate networks for potential security threats through the process of generating automated search queries. By identifying vulnerable websites, security experts can notify appropriate website owners and help fix vulnerabilities before they can be exploited by malicious actors.
To get the most out of Dork Generator, it is important to understand its capabilities and use them effectively. Some tips for using Dork generators:
Using Dork Generator:
1. Define your goal: Clearly state the purpose of the vulnerability assessment and the specific information or vulnerability you are looking for.
2. Choose the right Dork generator: Different Dork generators will have different features and functions. Choose a tool that matches your measurement goals.
3. Optimize your search queries: Try different search engines and terms to create precise queries that yield good results.
4. Analysis and analysis of results: Once you have the list of relevant websites, identify their vulnerabilities through rigorous analysis and penetration testing.
5. Maintain your conduct: It is important to follow ethical rules when using Dork generators. Obtain appropriate permissions and respect the privacy of the reviewed website.
Features of Dork Generators:
Although there are many features of different Dork generators, there are some similarities to look for:
Customer Review: Potential Nature creates advanced features using various search engine search engines.
Question customization: Flexibly customize your question by adding or removing search terms, and keywords.
Export and Reporting: Ability to export search results and generate reports for further analysis and documentation.
Proxy Support:
Option to use the name to display questions anonymously and eliminate the possibility of IP protection or detection.
Advantages of using Dork Generators
There are many advantages of using Dork Generators for vulnerability testing:
Dork Gen:
1. Runtime: Dork generator saves valuable time for network security professionals by automatically generating complex search criteria.
2. Full Detection: Using advanced detectors, Dork Generators can detect vulnerabilities that cannot be easily detected with traditional scanning methods.
3. Continuous monitoring: Dork Generators can be used to set up monitoring programs that regularly check websites for vulnerabilities and ensure security.
4. Cost Efficiency: Compared to traditional evaluation methods, Dork Generators offer more solutions, especially for large evaluations.
Limitations and Risks Associated with Dork Generators
While Dork Generators are useful tools, there are also limitations and risks associated with them:
1. False Positives: Dork Generator can be good. The site is marked as simple even though it is not actually simple. Validation and analysis are required to ensure the results are accurate.
2. Ethical decision: It is important that Dork Generators are used responsibly and respectfully and that appropriate approvals are obtained before making any evaluations.
3. Legal issues: Depending on the law, unauthorized copying of the website may be illegal. It is important to understand and comply with the rules, regulations and instructions.
Best Practices for Using Dork Generator
For efficient and responsible use of the Dork Generator, please consider the following best practices:
444 authorized by the owner of the website or 444
2 . Caution and etiquette: Respect yourself and observe etiquette when using the Dork Generator. Please do not access or use the information outside of public access.
3. Stay Current: Regularly update your Dork Generator software or scripts to take advantage of the latest features, bug fixes, and security patches.
4. Integration with other measurement systems: Dork Generators must be integrated with other non-standard measurement systems such as manual measurement and automatic scanners for comprehensive evaluation.
The future of Dork generators:
As cyber security continues to improve, the performance of Dork generators will also improve. Future improvements will include:
- Improved Query Construction Algorithms: More advanced algorithms that can generate specific queries and context-aware searches.
Integration with AI and ML: Dork generators can use AI and ML to increase accuracy and reduce false positives.
More automation and customization: More automation and customization options make it easier to test for vulnerabilities and meet specific requirements.
Result:
Dork Generators are essential tools for effective and efficient website evaluation. They can help cybersecurity professionals detect potential vulnerabilities by automatically generating search queries. However, it is important to use them responsibly, comply with ethical rules and obtain the necessary approvals. As technology continues to advance, Dork Generators' future in improving web security is bright.
FAQ:
1. Is it legal to use Dork generators?
The Dork generator is a legal device, but its use may be restricted by law. It is important to comply with the necessary laws and obtain the necessary permits before conducting a vulnerability assessment.
2. How accurate are the results obtained from Dork's generator?
The accuracy of the results depends on many factors, including the quality of the question design and the validation process. The vulnerability found by Dork Generators must be verified through further testing and penetration.
3. Can Dork Generators be used on a website?
Dork Generators can be used on any website; However, it is important to obtain permission from the site owner before conducting a vulnerability assessment.
4. Is Dork Generators the only way to do website vulnerability testing?
No, the Dork generator is just one tool in the website vulnerability testing arsenal. They should be used in conjunction with other methods such as manual assessment and automated printers for a comprehensive assessment.
5. Can stupid generators be used for crime?
Dork generators can be used within the scope of legitimate crime, provided that the necessary permits are obtained and legal practices are followed. Honest hackers use Dork Generators to identify vulnerabilities and help website owners improve their security measures.
Meta Description: Explore the effective skills of Splunk Enterprise Unlimited v9.0.five Full Activated, the complete information evaluation platform that permits groups to benefit from treasured insights and make knowledgeable decisions. Unlock the capacity of your information with superior functions and seamless activation. Read directly to find out how Splunk Enterprise can revolutionize your information evaluation manner.
Focus Keyword: Splunk Enterprise Unlimited v9.0.five Full Activated
Splunk Enterprise Unlimited v9.0.five Full Activated: Empowering Data Analysis and Insights:
Have you been looking for a complete information evaluation platform to take your commercial enterprise to new heights? Look no in addition to Splunk Enterprise Unlimited v9.0.five Full Activated. With its superior functions and seamless activation, this effective answer is designed that help you extract treasured insights from your information, optimize your operations, and pressure knowledgeable decision-making.
The Power of Splunk Enterprise Unlimited v9.0.five Full Activated:
Splunk Enterprise Unlimited v9.0.five Full Activated is today's information evaluation platform that offers groups with limitless capacity for exploring, reading, and visualizing information. By results easily collecting, indexing, and correlating information from numerous sources, Splunk Enterprise permits agencies to benefit from real-time visibility into their operations, discover anomalies, and pick out developments that may pressure increase performance.
Key Features and Benefits:
1. Streamlined Activation: With Splunk Enterprise Unlimited v9.0.five Full Activated, you could experience a hassle-loose activation manner that receives you up and going for walks quickly. Say goodbye to complicated setup tactics and begin harnessing the energy of Splunk proper away.
2. Data Collection and Indexing: Splunk Enterprise permits you to accumulate information from numerous sources, along with servers, applications, devices, and outside platforms. Its sturdy indexing skills make certain that your information is searchable, organized, and without problems on hand for evaluation.
3. Powerful Search and Analytics: Leverage Splunk's intuitive seek and analytics skills to convert uncooked information into actionable insights. Advanced seek functionalities, along with real-time searching, make it easy to drill down into particular events, patterns, and developments.
4. Visualizations and Dashboards: Splunk Enterprise Unlimited v9.0.five Full Activated gives an extensive variety of visualization options, allowing you to give your information in compelling and significant ways. Create interactive dashboards and reviews that may be shared throughout your corporation for advanced collaboration and decision-making.
Unlocking the Potential of Your Data:
In the modern information-pushed world, the potential to harness the energy of statistics is vital for commercial enterprise success. Splunk Enterprise Unlimited v9.0.five Full Activated empowers agencies to liberate the hidden capacity in their information, allowing them to:
- Gain Real-Time Insights: Splunk Enterprise permits you to reveal your information in real-time, offering on-the-spotaneous visibility into your operations. Detect anomalies, pick out safety threats, and proactively deal with problems earlier than they escalate.
- Optimize IT Operations: By reading machine-generated information, Splunk Enterprise allows you to proactively pick out and clear up IT problems. Improve machine performance, reduce downtime, and decorate the general performance of your IT infrastructure.
- Enhance Security and Compliance: Splunk Enterprise gives sturdy safety analytics skills, permitting you to discover and reply to capacity safety breaches promptly. Meet compliance requirements, pick out vulnerabilities, and enhance your corporation's safety posture.
- Improve Customer Experience: Utilize the insights derived from Splunk Enterprise to apprehend consumer behavior, preferences, and sentiment. Tailor your services and products to fulfill their desires and offer a customized enjoyment that units you other than the competition.
Conclusion:
Splunk Enterprise Unlimited v9.0.five Full Activated is the final answer for agencies searching for to unencumber the whole capacity in their statistics. With its superior functions, streamlined activation procedure, and effective seek and analytics talents, Splunk Enterprise empowers corporations to advantage of treasured insights, optimize operations, and make statistics-pushed selections.
By successfully gathering and indexing statistics from diverse assets, Splunk Enterprise presents real-time visibility into operations, allowing agencies to hit upon anomalies, become aware of trends, and power increase efficiency. The platform's intuitive seek functionalities and visualization alternatives permit customers to convert uncooked statistics into actionable insights, provided through interactive dashboards and reports.
With Splunk Enterprise Unlimited v9.0.five Full Activated, corporations can unencumber the genuine fee in their statistics. Gain real-time insights, optimize IT operations, beautify safety and compliance measures, and enhance purchaser experiences. Make knowledgeable selections primarily based totally on correct and complete statistics evaluation.
Don't omit the possibility of leveraging the electricity of Splunk Enterprise Unlimited v9.0.five Full Activated. Revolutionize your statistics evaluation procedure and live ahead of the competition. Activate Splunk Enterprise these days and unencumber the whole capacity of your statistics.
Get Started with Splunk Enterprise Unlimited v9.0.five Full Activated
Are you equipped to enjoy the transformative talents of Splunk Enterprise Unlimited v9.0?five Full Activated? Start harnessing the electricity of your statistics by following those easy steps:
1. Download and Install: Visit the reliable Splunk internet site and download the Splunk Enterprise Unlimited v9.0.five fully activated models. Follow the setup commands supplied to get the platform up and running.
2. Activate and Configure: Seamlessly spark off your Splunk Enterprise example with the use of the simplified activation procedure. Configure the platform in step with your precise enterprise needs, connecting the essential statistics reassets and customizing settings.
3. Explore and Analyze: Once activated, dive into the sector of statistics evaluation. Utilize Splunk Enterprise's effective seek and analytics functions to discover and examine your statistics. Create interactive visualizations and dashboards to offer your insights effectively.
4. Collaborate and Share: Share your findings and insights with colleagues and stakeholders throughout your organization. Enable collaboration and power knowledgeable decision-making through dispensing interactive dashboards and reports.
Unlock the electricity of your statistics with Splunk Enterprise Unlimited v9.0.five Full Activated. Discover new opportunities, optimize operations, and make statistics-pushed selections with confidence. Activate Splunk Enterprise these days and take your enterprise to new heights.
Note: Ensure that you are the use of a criminal and authorized model of Splunk Enterprise Unlimited v9.0.five fully activated for compliance with copyright and licensing regulations.
.
Stay ahead with Splunk Enterprise Unlimited v9.0.5 Full Launch Edition
Splunk Enterprise Unlimited v9.0.5 Full Launch Edition is the ultimate solution for businesses looking to leverage the power of data and gain a competitive advantage. Splunk Enterprise enables organizations to discover value, increase operational efficiency, and drive innovation by seamlessly collecting, indexing, and analyzing data from disparate sources.
Powerful features for advanced data analysis
1. Real-time data collection: Splunk Enterprise allows you to collect data in real-time from multiple computing sources with applications, servers, devices, and IoT sensors. This ensures you have up-to-date information so you can make timely decisions.
2. Scalable data indexing: With Splunk Enterprise, you can index and store large data sets for search and analysis. The scalable architecture of the platform allows you to manage data growth without compromising performance.
3. Advanced search capabilities: Splunk Enterprise provides advanced search capabilities that allow you to dig deep into your data. Conduct real-time searches, apply filters, and perform complex queries to uncover hidden patterns and relationships.
4. Customizable Dashboards: Visualize your data with interactive dashboards and reports customized to your specific needs. Customize the layout and add charts, graphs, and tables to create a visual summary of your data.
5. Machine learning integration: Leverage machine learning capabilities in Splunk Enterprise to enable vulnerability detection, predictive analytics, and quality monitoring. Identify potential problems before they impact your business.
Unlock insights across businesses:
Splunk Enterprise is a versatile platform used across businesses to drive success and innovation:
IT infrastructure efficiency 1.
2. Finance and Accounting: Analyze transaction data, identify fraud patterns and improve risk management.
3. Healthcare: Improve patient care, improve resource allocation, and ensure compliance.
5. Production: Monitor production processes, identify bottlenecks and improve operations.
H2: Launch Splunk Enterprise Unlimited v9.0.5 to unleash and unlock the potential of your data
Ready to unlock the full potential of your data? To download Splunk Enterprise Unlimited v9.0.5 full version, please follow the steps below:
1. Download the licensed version of Splunk Enterprise Unlimited v9.0.5 full version from the official Splunk website.
2. Follow the instructions to install the software on your preferred platform.
3. Activate your license using an activation key or activation key.
4. Configure Splunk Enterprise according to your organization's needs and connect your data source.
5. Start exploring your data with powerful search features, text filters and advanced search features.
6. Create custom dashboards and reports to visualize and share insights with stakeholders.
7. Continuously monitor and improve the data analysis process to derive maximum benefit from the data.
Empower your organization and unlock the insights hidden in your data with Splunk Enterprise Unlimited v9.0.5 Full Launch Edition. Make informed decisions, optimize operations and maintain a competitive advantage in today's data-driven world.
NOTE: It is important to use legal and licensed software in order to comply with applicable laws and licenses. Please ensure you are properly authorized for the full version of Splunk Enterprise Unlimited v9.0.5 before use.
Splunk Enterprise Unlimited v9.0.5 Full Launch: The Key to Data-Driven Success
In today's digital environment, the ability to analyze and leverage data is essential for businesses to be competitive. Splunk Enterprise Unlimited v9.0.5 is fully available and offers a comprehensive and powerful solution that enables organizations to unlock the true potential of their data. By leveraging Splunk Enterprise's advanced features, businesses can make informed decisions, streamline operations, and drive innovation.
Gain insight with advanced data analysis:
The full version of Splunk Enterprise Unlimited v9.0.5 provides a variety of features designed to enhance your data analysis Computational capacity:
44414.4 Instant data processing: With Splunk Enterprise, you can instantly collect and process data to track events and changes as they occur. This provides faster response times and the ability to resolve critical issues immediately.
2. Data flexibility: The platform supports data ingestion from multiple sources, including applications, servers, cloud platforms and IoT devices. Splunk Enterprise can process structured and unstructured data to provide a better view of your operations.
3. Smart Search: Splunk Enterprise provides powerful search capabilities that allow you to search your data and get useful information. Perform complex searches, apply filters, and drill down into specific data to uncover hidden patterns and patterns.
4. Advanced analysis: Leverage machine learning and statistical modeling in Splunk Enterprise to perform advanced analysis. Identify vulnerabilities, predict future events, and gain insights to guide your decision-making.
Business use:
Splunk Enterprise Unlimited v9.0.5 Fully Activated Trusted by organizations across the enterprise for its versatility and scalability. Here are some examples of how Splunk Enterprise is used in different areas:
Get More:
=========About Post===========
Clone Facebook Account
Caution ⚠️ ;This video is only for educational propose. don,t misuse
I Hope All Fine
I will Show How to clone Facebook Account 2023 New Method
Bio Raplika:
- apt update
- apt upgrade
- pkg install python
- pkg install python3
- apt install python -pip
- pip install responses
- pkg install git
- git clone https://github.com/shade234sherif/bio-replika
- pip install requirements.txt
- cd bio-replika
- python3 bio.py
Botol Baba:
World Old Cloning:
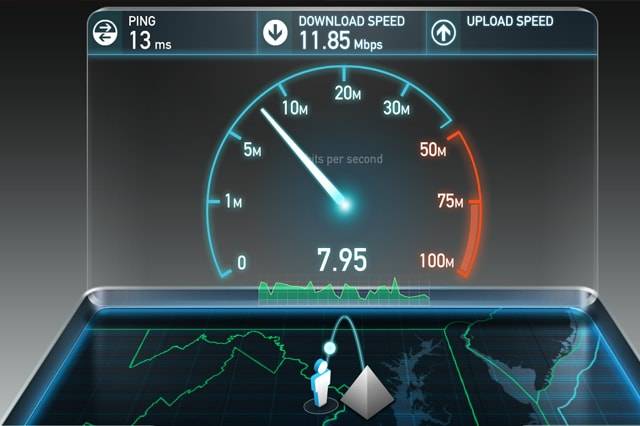
How Does Our Internet Speed Test Work?
A bandwidth speed test is an effective way for individuals and businesses to measure their connection. Broadband providers sell tiered packages based on speed, so it's important to test regularly to make sure you are getting the appropriate return on investment. For organizations that use VoIP services, reliable broadband speed is a core necessity for the daily work of every employee. From conference calls to exporting large amounts of data, the speed of your broadband connection has a huge impact on your bottom line.
Measure network performance with Speedtest
Speedtest is the definitive way to test the performance and quality of an internet connection. Since our founding in 2006, an unparalleled total of more than 40 billion consumer-initiated tests have been taken with Speedtest. Measure your download and upload speeds and check the quality of your video streaming experience all with a click of a button.
What are good internet speeds?
What is considered high-speed Internet 2022?
If you want to determine whether your ISP is living up to their promises, internet speed tests can help you out. There are quite a few technology companies offering speed tests, including Google Fiber. Is this a reliable speed test, or should you find another option?
Is 300 Mbps fast?
What is the max speed of Google Wifi?
Whats IP means?
(Internet Protocol)
Internet Protocol (IP) is the method or protocol by which data is sent from one computer to another on the internet. Each computer -- known as a host -- on the internet has at least one IP address that uniquely identifies it from all other computers on the internet.
Why is IP used?
In essence, IP addresses are the identifier that allows information to be sent between devices on a network: they contain location information and make devices accessible for communication. The internet needs a way to differentiate between different computers, routers, and websites.
.Feel Free To Write Imam Uddin
Get In Touch
Drop me a line, or give me a heads up if you have a plan for your Online Business! Simply write to me or find me in google. Also can contact with me on all popular social meadia by @imamuddinwp . I'd love to hear from you! My inbox is always open! 😎
Get In Touch!
I'm Social; Stay Connected!
.png)



.png)
